
6 Million Password Attacks In 16 Hours And How To Block Them
Last week in the President’s cyber security op-ed in the Wall Street Journal he implored Americans to move beyond simple passwords and to enable two factor authentication or cellphone sign-in. One of the things we monitor at Wordfence is the number of brute force attacks on WordPress websites. Brute force attacks are password guessing attacks, where an attacker tries to sign in as you by guessing your password.
To give you an idea of the level of attacks in the wild, we gathered data on brute force attacks across the sites we protect within a 16 hour Window starting Sunday until Monday (yesterday) at 2pm Pacific time. Here are the highlights. Remember, this is only over a 16 hour window which is relatively short. During this time we saw a total of 6,611,909 attacks targeting 72,532 individual websites. We saw attacks during this time from 8,941 unique IP addresses and the average number of attacks per victim website was 6.26.
The total number of attacking IP’s was actually 55,391 but we only counted IP’s that generated more than 10 failed logins across all sites. That way we excluded accidental login failures. So where are these attacks coming from. The results are not what you would expect. The table below shows the total number of attacks (brute force login attempts in this case) ordered by country: Brute Force Attacks by Country during our 16 hour window.
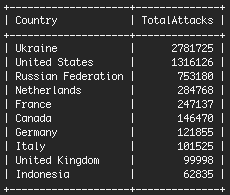
Brute Force Attacks by Country. The Ukraine is the top offender, but there is a specific reason for this which we explain below. The United States is second. Our hypothesis is that this is where most data centers are based and therefore most compromised sites, from which attacks are launched, will be based in the USA. You’ll notice that the Ukraine is at the top of the list. Over 86% of those attacks come from just two IP addresses at a Ukrainian hosting provider.
These two IP’s generated 2.4 Million attacks between the two of them. During just 16 hours, they targeted 37,454 unique victims. The two attackers that we analyzed are based at a Ukrainian hosting provider. They caused their Ukrainian hosting provider to account for more attacks than the next 19 hosting providers, combined. We currently aggregate attack information at a rate of 114 attacks per second. Analyzing data like this at Wordfence helps us understand the changing attack landscape and how to better protect our customers. What can you do to protect yourself?
Firstly, make sure you’re running the free or premium version of Wordfence and that you have the “Wordfence security network” feature enabled. It is enabled out of the box in Wordfence. With this feature enabled, if you get a failed login from an IP address, Wordfence will contact our cloud services to find out if that IP is one of the attackers we know about (like the two above). If it is, it will immediately be blocked from signing in, protecting your site from a brute force attack. The attacker won’t even get the standard 3 or 5 tries before they are locked out. Wordfence also provides login attempt limiting out of the box in the free and premium versions.
WordPress does not do this by default, so make sure you have this enabled. Next, as Obama suggests, enable cellphone sign-in for your WordPress website, also known as two factor authentication or 2FA. This feature is available in the Premium version of Wordfence and is easy to enable. You can learn more about cellphone sign-in on our documentation website. Perform a Password Audit Wordfence Premium gives you the ability to securely audit the strength of all your site member passwords, including your administrators. To launch this feature last year, we worked closely with our partners to build a supercomputer with over 40 Terraflops of processing power.
That is faster than the fastest computer in the world in 2003. Wordfence’s custom built password auditing hardware is pictured above. It is based in our data center in Lynnwood, Washington and uses very high performance GPU’s to audit the security of your passwords. By performing a password audit with Wordfence, you can launch a simulated password cracking attack on all site member passwords including administrators. Wordfence will then provide a report of which accounts suffer from weak passwords. Password Auditing is completely secure and uses a combination of hashing and public key cryptography to protect your data.
Once you receive the results, Wordfence provides a way for you to notify users they have a weak password or to force a password change. If you haven’t completed a password audit on your website, upgrade to Wordfence Premium and start an audit today. Go Deep on Password Security Password security is a big subject. To fully understand why strong passwords are important and how attackers target weak passwords, you need to gain an understanding of hashing, password salts and attack methods like rainbow tables, how salts work and why modern GPU’s give attackers a huge advantage. As part of our free WordPress Security Learning Center, we have created a comprehensive lesson that explains all of this and much more, including emerging improvements in password algorithms.
The lesson is designed to be a place that teachers and university professors can send their students to get a primer on password security and password authentication. If you invest the time to read this lesson, you will come away with a complete understanding of many fundamental security concepts that you will use throughout your career as a systems administrator.
Be warned, we don’t pull any punches. So if you do decide to dive in, make sure you make yourself a cup of something warm and allocate at least an hour to read the entire lesson. Once complete, you will have a well grounded understanding of password security, password authentication and modern attack techniques. We even throw in some number theory to help you understand what makes a password strong.
To give you an idea of the level of attacks in the wild, we gathered data on brute force attacks across the sites we protect within a 16 hour Window starting Sunday until Monday (yesterday) at 2pm Pacific time. Here are the highlights. Remember, this is only over a 16 hour window which is relatively short. During this time we saw a total of 6,611,909 attacks targeting 72,532 individual websites. We saw attacks during this time from 8,941 unique IP addresses and the average number of attacks per victim website was 6.26.
The total number of attacking IP’s was actually 55,391 but we only counted IP’s that generated more than 10 failed logins across all sites. That way we excluded accidental login failures. So where are these attacks coming from. The results are not what you would expect. The table below shows the total number of attacks (brute force login attempts in this case) ordered by country: Brute Force Attacks by Country during our 16 hour window.

Brute Force Attacks by Country. The Ukraine is the top offender, but there is a specific reason for this which we explain below. The United States is second. Our hypothesis is that this is where most data centers are based and therefore most compromised sites, from which attacks are launched, will be based in the USA. You’ll notice that the Ukraine is at the top of the list. Over 86% of those attacks come from just two IP addresses at a Ukrainian hosting provider.
These two IP’s generated 2.4 Million attacks between the two of them. During just 16 hours, they targeted 37,454 unique victims. The two attackers that we analyzed are based at a Ukrainian hosting provider. They caused their Ukrainian hosting provider to account for more attacks than the next 19 hosting providers, combined. We currently aggregate attack information at a rate of 114 attacks per second. Analyzing data like this at Wordfence helps us understand the changing attack landscape and how to better protect our customers. What can you do to protect yourself?
Firstly, make sure you’re running the free or premium version of Wordfence and that you have the “Wordfence security network” feature enabled. It is enabled out of the box in Wordfence. With this feature enabled, if you get a failed login from an IP address, Wordfence will contact our cloud services to find out if that IP is one of the attackers we know about (like the two above). If it is, it will immediately be blocked from signing in, protecting your site from a brute force attack. The attacker won’t even get the standard 3 or 5 tries before they are locked out. Wordfence also provides login attempt limiting out of the box in the free and premium versions.
WordPress does not do this by default, so make sure you have this enabled. Next, as Obama suggests, enable cellphone sign-in for your WordPress website, also known as two factor authentication or 2FA. This feature is available in the Premium version of Wordfence and is easy to enable. You can learn more about cellphone sign-in on our documentation website. Perform a Password Audit Wordfence Premium gives you the ability to securely audit the strength of all your site member passwords, including your administrators. To launch this feature last year, we worked closely with our partners to build a supercomputer with over 40 Terraflops of processing power.
That is faster than the fastest computer in the world in 2003. Wordfence’s custom built password auditing hardware is pictured above. It is based in our data center in Lynnwood, Washington and uses very high performance GPU’s to audit the security of your passwords. By performing a password audit with Wordfence, you can launch a simulated password cracking attack on all site member passwords including administrators. Wordfence will then provide a report of which accounts suffer from weak passwords. Password Auditing is completely secure and uses a combination of hashing and public key cryptography to protect your data.
Once you receive the results, Wordfence provides a way for you to notify users they have a weak password or to force a password change. If you haven’t completed a password audit on your website, upgrade to Wordfence Premium and start an audit today. Go Deep on Password Security Password security is a big subject. To fully understand why strong passwords are important and how attackers target weak passwords, you need to gain an understanding of hashing, password salts and attack methods like rainbow tables, how salts work and why modern GPU’s give attackers a huge advantage. As part of our free WordPress Security Learning Center, we have created a comprehensive lesson that explains all of this and much more, including emerging improvements in password algorithms.
The lesson is designed to be a place that teachers and university professors can send their students to get a primer on password security and password authentication. If you invest the time to read this lesson, you will come away with a complete understanding of many fundamental security concepts that you will use throughout your career as a systems administrator.
Be warned, we don’t pull any punches. So if you do decide to dive in, make sure you make yourself a cup of something warm and allocate at least an hour to read the entire lesson. Once complete, you will have a well grounded understanding of password security, password authentication and modern attack techniques. We even throw in some number theory to help you understand what makes a password strong.

